 Online services have become an essential part of all modern organizations. Although they increase efficiency, they also expose your network to security risks. Most malicious users gain access to cyber systems through unprotected or easily compromised network ports.
Online services have become an essential part of all modern organizations. Although they increase efficiency, they also expose your network to security risks. Most malicious users gain access to cyber systems through unprotected or easily compromised network ports.
Challenges of Developing a Network Security Plan
Each security layer you add to your network impacts user experience. It increases operating and capital expenditure costs. Real-time network traffic scans also use a huge chunk of your computing resources.
An ideal plan is one that secures your network at a manageable budget without compromising on the UX. Answering the following questions helps you develop a comprehensive cybersecurity plan:
- Which aspects of our network are most vulnerable?
- Which government and industry regulations must we comply with?
- How will we audit the network security plan once it’s implemented?
- Which tools will we need to detect and prevent the latest, most sophisticated breach attempts?
Essential Steps to Follow

The most important steps in developing and implementing a solid network security plan include:
1. Assessing Your Network
This involves evaluating all hardware and software components of your network. You should also monitor both incoming and outgoing traffic so as to identify potential access points. Setting strict network access permissions makes it easier to identify breaches.
2. Planning
Once the assessment is complete, you’ll have a clearer picture of your exact security needs. You can also figure out which experts you need to design, implement, and maintain a better network security solution.
Planning involves deciding on whether to replace or upgrade vulnerable components, integrating new software, and improving network access permissions. You can also research on the latest encryption methods, secure remote access methods, and how to respond to specific threats.
3. Installation
Smooth deployment depends on how detailed the planning phase was. Since your network runs 24/7, this critical task should ideally be performed when traffic is at its lowest.
If deploying the security plan in one instance is likely to cause network interference, you may do it in phases. Address the most critical vulnerabilities first. Holding trials before going live makes it easier to identify and solve 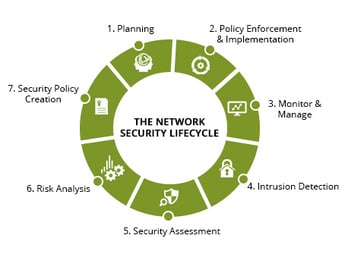 previously unforeseen issues.
previously unforeseen issues.
4. Constant monitoring
Having the best network security system doesn’t mean you should rest on your laurels. Malicious attackers are constantly probing your network for weak points. Reviewing your audit logs gives you relevant information on potential threats.
It also allows you to tweak your security settings to prevent similar attacks in the future. You should also have a team of IT experts specifically tasked with responding to breaches. They can do this by resetting passwords, redefining security levels, and switching off vulnerable parts of the network.
How to Keep Your Network Secure
As part of your overall cybersecurity blueprint, a top-notch network security solution should follow a well-defined strategy. This includes:
Isolating and Segmenting Networks
Instead of treating your network as a single entity, segment it according to the types of traffic flowing through it. Creating sub-networks allows you to lock out some users from sensitive parts. It’s easier to contain a breach by isolating the relevant sub-network and neutralizing the threat before opening it again. During this period, operations in other networks can carry on undisturbed.
Creating a Security-Focused Culture
As sophisticated as your security system might be, you can’t ignore the human factor. Ensure your employees are updated on basic cybersecurity measures, even if they’re not in the IT department.
factor. Ensure your employees are updated on basic cybersecurity measures, even if they’re not in the IT department.
This includes identifying and reporting suspected phishing attempts and social engineering attacks. Hold regular training sessions on common network vulnerabilities and how to prevent them. Some companies create fake network attacks to gauge their employees’ level of preparedness.
Secure Wireless Networks
Wireless networks have become a vital part of every organization’s cyber system. Although they improve service delivery, they also make it easier for bad actors to gain access to your network.
Your network security plan must include your Wi-Fi network. You can upgrade it by changing or masking your SSID, encrypting wireless access points, adding two-factor authentication, and changing passwords.
Hiring a Managed Service Provider (MSP)
An in-house IT team helps you manage your day-to-day tech challenges, but a managed services provider takes it to the next level. Such firms are highly specialized in solving the most complex cybersecurity problems. Their services include performing security audits, implementing new security updates and testing your network for vulnerabilities. While they charge premium rates, the superior services offered by MSPs result in several long term benefits for your company.
Ready to Develop Your Network Security Plan?
Hummingbird Networks is your one-stop-shop for end-to-end network security solutions. Over the past 15 years, we’ve established ourselves as the go-to IT partner for several organizations.
Our customers, ranging from startups to large corporations, enjoy the most secure and efficient networks available. Contact us today for more information on our wide range of IT solutions.









