
A Comparison Of The Best Cloud Solutions For Your Business
Cloud Computing

Powerful, Cloud-Managed Security With Cisco Meraki MX
Meraki

Optimize Your Network Setup With The Best Meraki Switches
Meraki | Switches

How Cloud Networking Helps Businesses Stay Ahead
Networking
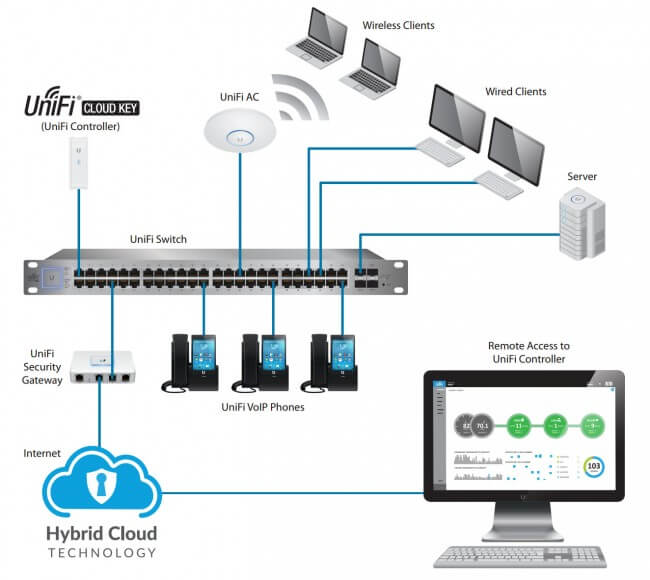
Ubiquiti’s UniFi Cloud Key - What is it?
Ubiquiti

Building a Scalable Wi-Fi Network - Let it Grow!
Wireless
The Five Pillars Of SASE
Cisco | Network Security | SASE | SD-WAN
Why Upgrading to Windows 11 is Essential: Myths & Transition Tips
Buyers Guides | BYOD | Hybrid Work | Networking | Small Business
Best Wireless Access Point for Optimal Performance

Top 11 Cisco Meraki Switches And Why They’re The Best Choice
Meraki

